LuaDream Malware
Original Issue Date:-
October 03, 2023
Virus Type:- Backdoor malware
Severity:-
Medium
It has been reported that a newly surfaced info-stealing malware, named 'LuaDream,' is spreading across the globe. The threat actors, tagged as Sandman, targeting the telecommunications sector in various regions to pose significant risks to victims, including potential data theft and further malicious activities.
Infection Mechanism:
The malicious campaign utilizes DLL hijacking for its operation. LuaDream combines 34 components, encompassing both core and support elements. These components leverage the LuaJIT bytecode and the ffi library to interact with the Windows API.
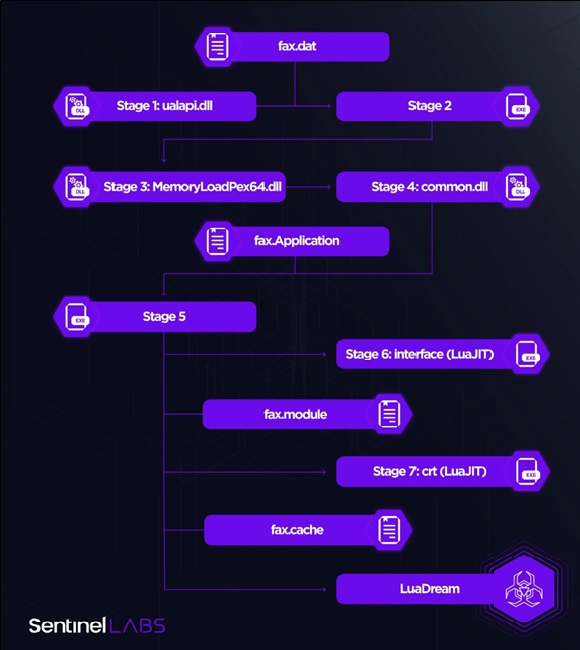
The core components are responsible for executing the malware's essential tasks, such as system and user data collection, plugin control, and C2 communications, while the support components focus on technical aspects, including the provision of Lua libraries and Windows API definitions.
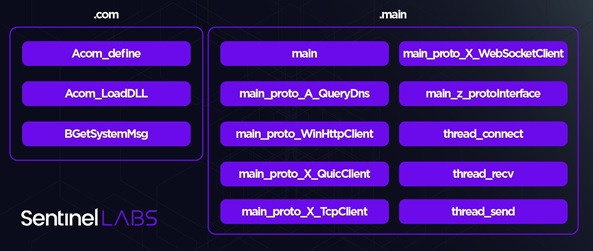
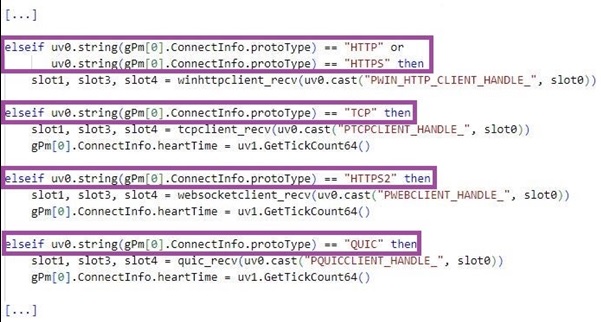
When LuaDream is initialized, it establishes a connection with a C2 server using WebSocket, TCP, HTTPS, or QUIC protocols, and transmits collected data, which contains details such as malware versions, IP-MAC addresses, OS information, and more.
LuaDream is a multi-component backdoor with capabilities to manage plugins, exfiltrate system data, and steal user data through multiple protocols.
The Sandman threat actors steal the admin credentials to gain access to the network of the organization. Threat actors are observed using 'pass-the-hash' attacks, extracting and reusing NTLM hashes stored in memory to authenticate with remote servers and services after breaching the network.
As LuaDream receives commands from C2 servers to collect data and manage plugins for execution on target systems, it poses a range of potential adverse outcomes, encompassing data breaches, financial losses, infringements on privacy, and disruptions to system functionality. Furthermore, it jeopardizes personal and sensitive information.
It is also observed that threat actors operate LuaDream covertly to evade detection and maintain long-term access to systems.
Indicator of Compromise:
Hashes:
| SHA 1 | File name |
|---|---|
| 1cd0a3dd6354a3d4a29226f5580f8a51ec3837d4 | fax.dat |
| 27894955aaf082a606337ebe29d263263be52154 | fax.Application |
| 5302c39764922f17e4bc14f589fa45408f8a5089 | ualapi.dll |
| 77e00e3067f23df10196412f231e80cec41c5253 | fax.cache |
| b9ea189e2420a29978e4dc73d8d2fd801f6a0db2 | UpdateCheck.dll |
| fb1c6a23e8e0693194a365619b388b09155c2183 | updater.ver |
| ff2802cdbc40d2ef3585357b7e6947d42b875884 | fax.module |
LuaDream Folder File paths:
- %ProgramData%\FaxConfig
- %ProgramData%\FaxLib
C2 Server Domains:
- mode.encagil[dot]com<1-24>
- ssl.explorecell[dot]com
Countermeasures:
- Do not download and install applications from untrusted sources [offered via unknown websites/ links on unscrupulous messages]. Install applications downloaded from reputed application market only. Users must be aware while clicking on links during web search.
- Update software and operating systems with the latest patches. Outdated applications and operating systems are the targets of most attacks.
- Don't open attachments in unsolicited e-mails, even if they come from people in your contact list, and never click on a URL contained in an unsolicited e-mail, even if the link seems benign. In cases of genuine URLs close out the e-mail and go to the organization’s website directly through browser.
- It is advised to block office applications from creating executable files.
- Install ad blockers to combat exploit kits such as Fallout that are distributed via malicious advertising.
- Prohibit external FTP connections and blacklist downloads of known offensive security tools.
- All operating systems and applications should be kept updated on a regular basis. Virtual patching can be considered for protecting legacy systems and networks. This measure hinders cybercriminals from gaining easy access to any system through vulnerabilities in outdated applications and software. Avoid applying updates / patches available in any unofficial channel.
- Restrict execution of Power shell /WSCRIPT in an enterprise environment. Ensure installation and use of the latest version of PowerShell, with enhanced logging enabled. Script block logging and transcription enabled. Send the associated logs to a centralized log repository for monitoring and analysis. https://www.fireeye.com/blog/threat-research/2016/02/greater_visibilityt.html
- Establish a Sender Policy Framework (SPF) for your domain, which is an email validation system designed to prevent spam by detecting email spoofing by which most of the ransomware samples successfully reaches the corporate email boxes.
- Application whitelisting/Strict implementation of Software Restriction Policies (SRP) to block binaries running from %APPDATA% and %TEMP% paths. Ransomware sample drops and executes generally from these locations.
- Users are advised to disable their RDP if not in use, if required, it should be placed behind the firewall and users are to bind with proper policies while using the RDP.
- Block the attachments of file types, exe|pif|tmp|url|vb|vbe|scr|reg|cer|pst|cmd|com|bat|dll|dat|hlp|hta|js|wsf
- Consider encrypting the confidential data as the ransomware generally targets common file types.
- Perform regular backups of all critical information to limit the impact of data or system loss and to help expedite the recovery process. Ideally, this data should be kept on a separate device, and backups should be stored offline.
- Network segmentation and segregation into security zones - help protect sensitive information and critical services. Separate administrative network from business processes with physical controls and Virtual Local Area Networks.
References:


