Mallox Ransomware
Original Issue Date:-
July 25, 2023
Virus Type:- Ransomware
Severity:-
High
It has been observed that Mallox Ransomware is currently targeting unsecured Microsoft SQL Servers, using them as entry points into victims ICT infrastructures to distribute the ransomware.It has also been observed that the threat actor group has used brute force techniques on publicly exposed MS SQL instances to gain initial access to the victims network infrastructure.
Mallox ransomware, like many other ransomware threats, follows the double extortion technique: it steals data before encrypting an organization's files and then threatens to publish the stolen data on the leak site as leverage to convince victims to pay the ransom fee.
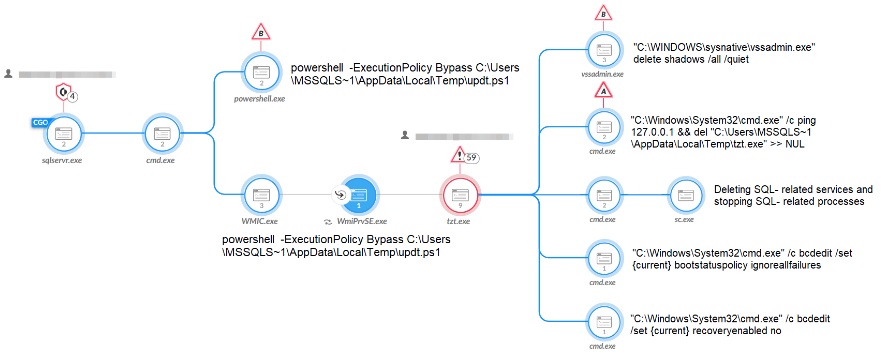
The following figure shows the process of the Mallox Ransomware attack.
Indicator of Compromise:
For the detailed IoC, kindly click Indicators of Compromise
Best Practices and Recommendations:
- Do not expose SQL Servers on the default port (1433) over the Internet:- The default port (1433) is well known and is often targeted by hackers and malicious actors looking for vulnerable servers to exploit. Instead, consider using a VPN or other secure connection to access your SQL servers.
- Disable the sa account:- The sa (system administrator) account has the highest level of privileges in SQL Server. Disable this account or change its password to something very strong to reduce the risk of unauthorized access.
- Audit SQL CLR Assemblies:- Disable SQL CLR assemblies if not needed. Establish an auditing procedure to regularly check the existing CLR assemblies and remove any unwanted assemblies.
- Use a firewall:- Use a firewall to restrict access to your SQL servers. Only allow incoming traffic from trusted networks and IP addresses. Block all incoming traffic on port 1433 except for authorized users.
- Keep your SQL Server up to date:- Install the latest updates and patches for your SQL Server instance to keep it secure and protect against known vulnerabilities.
- Use strong and unique passwords:- Make sure that all SQL logins have strong and unique passwords that are difficult to guess. Use a combination of upper and lower case letters, numbers, and special characters.
- Use account lockout policies:- Configure account lockout policies to lock out SQL Server logins after a certain number of failed login attempts. This can help protect against brute force attacks.
- Use SSL/TLS to encrypt data in transit:- Use SSL/TLS to encrypt data in transit between clients and your SQL servers. This can help protect against eavesdropping and other types of attacks.
- Monitor your SQL Server:- Use SQL Server auditing to track and log all activity on your SQL Server instance. This can help you detect and respond to security threats in a timely manner.
- For detailed recommendations, please refer to "Best Practices and Remedial Measures" at https://www.csk.gov.in/alerts/ransomware.html
References:


