Nexus Android Banking Trojan
Original Issue Date:-
April 24, 2023
Virus Type:- Android Banking Trojan
Severity:-
Medium
It has been reported that a malware campaign spreading Nexus Android banking trojan through Malware-as-a-Service (MaaS) platform is active. The campaign is active on underground/private forums where threat actor provides it on a subscription basis. Nexus is a framework for Account Takeover attacks (ATO) through which Threat Actors attack target application. Its major focus is on targeting banking portals & cryptocurrency services such as credential stealing and SMS interception. The image below represents the advertisement for the malware:
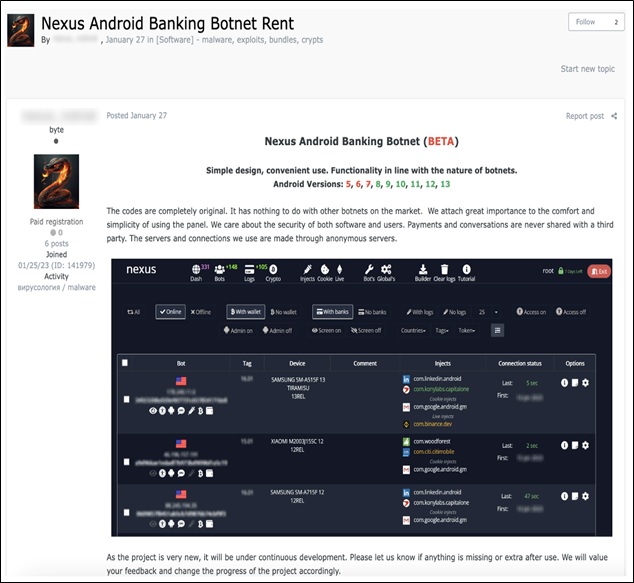
In thread, the threat actor (TA) also displays the list of its target applications.
The components of Nexus show somewhat similarity with earlier developed banking trojan called SOVA. It contains a ransomware module also which seems to be under active development.
Infection Mechanism
As observed, the Nexus is seen distributed through phishing campaign impersonating legitimate website. The Nexus botnet focuses on stealing the credentials from banking apps and even 2FA authentication of Google Authenticator through the abusing accessibility service. It can steal SMS, crypto wallets and cookies of websites also. Over the time, the malware has enriched in its capability of stealing the information, and further malicious activity.
Once the malware is installed on victim's device, it connects to C2 server for command control and activity. It further provides a C2 web panel for attackers to carry out their attacks and acquire stolen data.Nexus C2 web panel exposes the login page on the internet.
After login, it provides visibility to botnet status, injection etc. As observed, the Nexus malware requests the users for different permissions, and abuses which abuses as its functional requirements such as permissions related to SMS, contacts and storage etc.
Upon launching, the malware asks for accessibility service and once it is allowed, it itself abuse this to approve other permissions, administration rights, keylogging activities.
The malware operates through Command and Control (C&C) server and transmits sensitive information such as Accessibility logs and a list of installed applications etc.
After receiving the list of applications from the victim’s device, Threat Actor (TA) match that with the targeted banking application and If any one matches, the C&C server sends an “enableinject” command, including the specific application’s package name.
Then it downloads the HTML injection code for the targeted application on the victim's device. The HTML injection code works as a phishing page for the targeted application. Whenever the user uses the that targeted application, the code launches the WebView interface. Through this, the TA obtains the credentials. It includes a ransomware module which is used to encrypt files on victim device.
Indicator of Compromise:
SHA256- 3dcd8e0cf7403ede8d56df9d53df26266176c3c9255a5979da08f5e8bb60ee3f : Nexus APK
- 1c99c658e30c672927dccbd8628107abf36d990d : Nexus APK
- d87e04db4f4a36df263ecbfe8a8605bd : Nexus APK
- hxxp://5.161.97[.]57:5000
Best Practices and Recommendations:
- Reduce the risk of downloading potentially harmful apps by limiting your download sources to official app stores, such as your device’s manufacturer or operating system app store.
- Prior to downloading / installing apps on android devices (even from Google Play Store):
- Always review the app details, number of downloads, user reviews, comments and "ADDITIONAL INFORMATION" section.
- Verify app permissions and grant only those permissions which have relevant context for the app's purpose.
- Do not check "Untrusted Sources" checkbox to install side loaded apps.
- Install Android updates and patches as and when available from Android device vendors.
- Google Play Protect should be enabled on Android device.
- Permissions should also be given carefully.
- Do not browse un-trusted websites or follow un-trusted links and exercise caution while clicking on the link provided in any unsolicited emails and SMSs.
- Install and maintain updated anti-virus and antispyware software.
- Look for suspicious numbers that don't look like real mobile phone numbers. Scammers often mask their identity by using email-to-text services to avoid revealing their actual phone number. Genuine SMS messages received from banks usually contain sender id (consisting of bank’s short name) instead of a phone number in sender information field.
- Do extensive research before clicking on link provided in the message. There are many websites that allow anyone to run search based on a phone number and see any relatable information about whether or not a number is legit.
- Only click on URLs that clearly indicate the website domain. When in doubt, users can search for the organisation's website directly using search engines to ensure that the websites they visited are legitimate.
- Consider using Safe Browsing tools, filtering tools (antivirus and content-based filtering) in your antivirus, firewall, and filtering services.
- Exercise caution towards shortened URLs, such as those involving bit.ly and tinyurl. Users are advised to hover their cursors over the shortened URLs (if possible) to see the full website domain which they are visiting or use a URL checker that will allow the user to enter a short URL and view the full URL. Users can also use the shortening service preview feature to see a preview of the full URL.
- Look out for valid encryption certificates by checking for the green lock in the browser's address bar, before providing any sensitive information such as personal particulars or account login details.
- Customer should report any unusual activity in their account immediately to the respective bank with the relevant details for taking further appropriate actions.
References:
- https://blog.cyble.com/2023/03/09/nexus-the-latest-android-banking-trojan-with-sova-connections/
- https://www.cleafy.com/cleafy-labs/nexus-a-new-android-botnet
- https://thehackernews.com/2023/03/nexus-new-rising-android-banking-trojan.html
- https://www.techrepublic.com/article/nexus-android-malware-finance-targets/


