Ramnit Banking Trojan
Original Issue Date:-
November 02, 2023
Virus Type:- Banking Trojan
Severity:-
Medium
It has been reported that a trojan dubbed as “Ramnit”, which can steal sensitive data like personal information, banking credentials, FTP passwords, and session cookies is spreading across the globe.
Infection Mechanism
In attacking campaign, a spear-phishing email is used to target the victim, containing a hyperlink leading to a compromised website. Upon clicking the hyperlink and accessing the site, the victim is prompted to download an additional payload, specifically a compressed ZIP file which contains both, a harmless .jpg file and a .lnk shortcut file. The .lnk file is cleverly disguised as a standard Windows folder, complete with an inconspicuous icon.
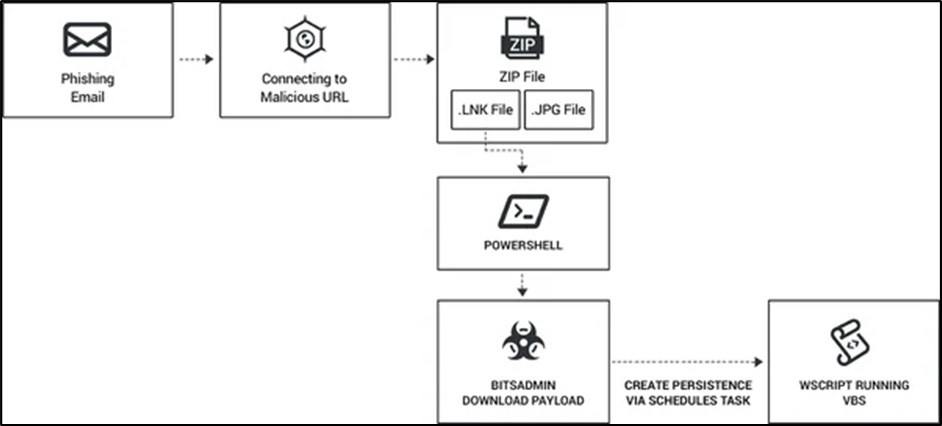
Upon clicking the .lnk shortcut file, a Command Prompt window is triggered, initiating the execution of obfuscated commands in a PowerShell process.
The .lnk file's PowerShell script is responsible for fetching the sLoad banking Trojan dropper, which possesses capabilities for reconnaissance, information gathering, screen capturing, and command and control functions.
SLoad, a tool that compiles data from the Win32_LogicalDisk data source, representing local storage devices on Windows computers, additionally captures details concerning network shares and physical devices via the NET VIEW command.
SLoad primarily gathers information by employing screen capture. Ramnit trojan fabricate a scheduled task to maintain its obfuscation. It also tries to bypass AMSI framework. The malware contains several module including one to communicate to C2.
Indicator of Compromise:
IP:- 185.197.75[.]10
- B564ED3DE7A49673AC19B6231E439032AE6EAA68
- 7FDBCB40E0BE3563B7093F32F4B2967A0550437F
- bureaucratica[dot]org
- packerd[dot]me
- image.orchas[dot]com
For more detailed list of IoC, kindly refer the below URL:
Best Practices and Recommendations:
- Reduce the risk of downloading potentially harmful apps by limiting your download sources to official app stores, such as your device’s manufacturer or operating system app store.
- Prior to downloading / installing apps on android devices (even from Google Play Store):
- Always review the app details, number of downloads, user reviews, comments and "ADDITIONAL INFORMATION" section.
- Verify app permissions and grant only those permissions which have relevant context for the app's purpose.
- Do not check "Untrusted Sources" checkbox to install side loaded apps.
- Install Android updates and patches as and when available from Android device vendors.
- Google Play Protect should be enabled on Android device.
- Permissions should also be given carefully.
- Do not browse un-trusted websites or follow un-trusted links and exercise caution while clicking on the link provided in any unsolicited emails and SMSs.
- Install and maintain updated anti-virus and antispyware software.
- Look for suspicious numbers that don't look like real mobile phone numbers. Scammers often mask their identity by using email-to-text services to avoid revealing their actual phone number. Genuine SMS messages received from banks usually contain sender id (consisting of bank’s short name) instead of a phone number in sender information field.
- Do extensive research before clicking on link provided in the message. There are many websites that allow anyone to run search based on a phone number and see any relatable information about whether or not a number is legit.
- Only click on URLs that clearly indicate the website domain. When in doubt, users can search for the organisation's website directly using search engines to ensure that the websites they visited are legitimate.
- Consider using Safe Browsing tools, filtering tools (antivirus and content-based filtering) in your antivirus, firewall, and filtering services.
- Exercise caution towards shortened URLs, such as those involving bit.ly and tinyurl. Users are advised to hover their cursors over the shortened URLs (if possible) to see the full website domain which they are visiting or use a URL checker that will allow the user to enter a short URL and view the full URL. Users can also use the shortening service preview feature to see a preview of the full URL.
- Look out for valid encryption certificates by checking for the green lock in the browser's address bar, before providing any sensitive information such as personal particulars or account login details.
- Customer should report any unusual activity in their account immediately to the respective bank with the relevant details for taking further appropriate actions.
References:


