Royal Ransomware
Original Issue Date:-
May 02, 2023
Virus Type:- Ransomware
Severity:-
Medium
It has been reported that a ransomware, dubbed “Royal ransomware” is targeting multiple crucial infrastructure sectors including manufacturing, communications, healthcare, education, etc. or individuals. The ransomware encrypts the files on a victim's system and attackers ask for ransom payment in bitcoin. Attackers also threaten to leak the data in public domain also if denied payment.
Like many ransomwares, royal ransomware is spread through phishing emails, malicious downloads, abusing RDP and other forms of social engineering. Threat actors have followed many tactics to mislead victims into installing the remote access software as a part of callback phishing, where they pretend to be various service providers.
Infection Mechanism
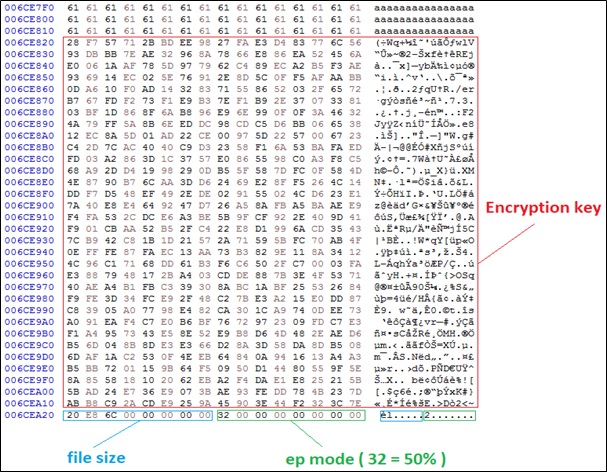
Royal ransomware uses a specific approach to encrypt files depending on size of content. It will divide the content into two segments i.e. encrypted and unencrypted. The malware may choose a small amount of data from a large file to encrypt so as to increase the chances of avoiding caution or detection. The ransomware adds 532 bytes at the end of encrypted file for writing randomly generated encrypted key, file size of encrypted file and encryption percentages parameter.
The threat actors get access to the victim's system in multiple ways, below are few of them:
- Threat Actors mostly approach Phishing emails that contain malicious documents, advertisements, links, etc. Whenever a victim downloads or clicks on the malicious part unknowingly then it paves the way for malware infection.
- Getting access when Remote Desktop Protocol compromises.
- To gain access to the system they exploit the public-facing applications.
- Taking the service of brokers to get access by harvesting the VPN and other network credentials from the logs.
Once the threat actors get access to the victim's network, they interact with the command and control (C2) and download or transfer the tools into a compromised environment. Before starting encryption, the ransomware checks the state of targeted files and delete shadow copies to prevent recovery through service (vssadmin.exe). After intruding into network, the malware tries to make persistence and lateral movement in the network. Even after getting access of domain controller, the ransomware disables anti-virus protocols. Moreover, the ransomware exfiltrates a large amount of data before encryption.
It adds the ".royal" extension to the encrypted file names. For example, a file named "example.jpg" would be renamed to "example.jpg.royal" after it was encrypted by the malware.
It is also observed that Royal ransomware does not share the ransom information like demanded ransom amount, any instructions, etc. on a note like other ransomware, instead of this Royal actors like to connect with the victim directly via a .onion URL route (dark web TOR browser) so they only share the URL on an initial ransom note after encryption. The note will be in README.TXT format.
An encrypted directory will appear as follows:
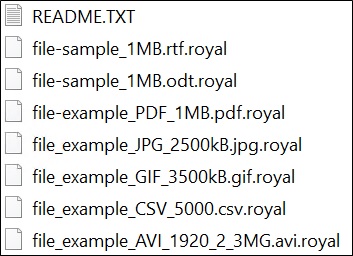
As observed, the ransomware uses several tools, software to perform its sequential malicious activities.
Indicator of Compromise:
Malicious IPs:
- 102.157.44[dot]105
- 105.158.118[dot]241
- 105.69.155[dot]85
- 113.169.187[dot]159
Malicious Domains:
- ciborkumari[dot]xyz
- sombrat[dot]com
- gororama[dot]com
- softeruplive[dot]com
For more detailed list of IOC (Malicious IP, Domain & Hashes) kindly refer the URL:
Best Practices and Recommendations:
- Maintain offline backups of data, and regularly maintain backup and restoration. This practice will ensure the organization will not be severely interrupted, have irretrievable data.
- Ensure all backup data is encrypted, immutable (i.e., cannot be altered or deleted) and covers the entire organization’s data infrastructure.
- Implement all accounts with password logins (e.g., service account, admin accounts, and domain admin accounts) to have strong, unique passwords.
- Implement multi-factor authentication for all services to the extent possible, particularly for webmail, virtual private networks, and accounts that access critical systems.
- Remove unnecessary access to administrative shares.
- Use a host-based firewall to only allow connections to administrative shares via server message block (SMB) from a limited set of administrator machines.
- Enable protected files in the Windows Operating System to prevent unauthorized changes to critical files.
- Disable remote Desktop Connections, employ least-privileged accounts. Limit users who can log in using Remote Desktop, set an account lockout policy. Ensure proper RDP logging and configuration.
- Check regularly for the integrity of the information stored in the databases.
- Ensure integrity of the codes /scripts being used in database, authentication and sensitive system.
- Establish Domain-based Message Authentication, Reporting, and Conformance (DMARC), Domain Keys Identified Mail (DKIM) and Sender Policy Framework (SPF) for your domain, which is an email validation system designed to prevent spam by detecting email spoofing by which most of the ransomware samples successfully reaches the corporate email boxes.
- Keep the operating system, third party applications (MS office, browsers, browser Plugins) up-to-date with the latest patches.
- Application white listing/Strict implementation of Software Restriction Policies (SRP) to block binaries running from %APPDATA% and %TEMP% paths. Ransomware sample drops and executes generally from these locations.
- Maintain updated Antivirus software on all systems.
- Don't open attachments in unsolicited e-mails, even if they come from people in your contact list, and never click on a URL contained in an unsolicited e-mail, even if the link seems benign. In cases of genuine URLs close out the e-mail and go to the organization's website directly through browser.
- Follow safe practices when browsing the web. Ensure the web browsers are secured enough with appropriate content controls.
- Network segmentation and segregation into security zones - help protect sensitive information and critical services. Separate administrative network from business processes with physical controls and Virtual Local Area Networks.
- Disable ActiveX content in Microsoft Office applications such as Word, Excel, etc.
- Restrict access using firewalls and allow only to selected remote endpoints, VPN may also be used with dedicated pool for RDP access.
- Use strong authentication protocol, such as Network Level Authentication (NLA) in Windows.
- Additional Security measures that may be considered are:
- Use RDP Gateways for better management.
- Change the listening port for Remote Desktop.
- Tunnel Remote Desktop connections through IPSec or SSH.
- Two-factor authentication may also be considered for highly critical systems.
- If not required consider disabling PowerShell / windows script hosting.
- Restrict users' abilities (permissions) to install and run unwanted software applications.
- Enable personal firewalls on workstations.
- Implement strict External Device (USB drive) usage policy.
- Employ data-at-rest and data-in-transit encryption.
- Consider installing Enhanced Mitigation Experience Toolkit, or similar host-level anti-exploitation tools.
- Block the attachments of file types, exe|pif|tmp|url|vb|vbe|scr|reg|cer|pst|cmd|com|bat|dll|dat|hlp|hta|js|wsf
- Carry out vulnerability Assessment and Penetration Testing (VAPT) and information security audit of critical networks/systems, especially database servers from CERT-IN empanelled auditors. Repeat audits at regular intervals.
- Individuals or organizations are not encouraged to pay the ransom, as this does not guarantee files will be released. Report such instances of fraud to CERT-In and Law Enforcement agencies.
References:
- https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-061a
- https://www.cybereason.com/blog/royal-ransomware-analysis
- https://www.malwarebytes.com/blog/news/2023/03/warning-issued-over-royal-ransomware
- https://www.bleepingcomputer.com/news/security/fbi-and-cisa-warn-of-increasing-royal-ransomware-attack-risks
- https://techcrunch.com/2023/03/03/us-government-royal-ransomware-advisory/
- https://www.csk.gov.in/alerts/ransomware.html


