Shampoo ChromeLoader malware
Original Issue Date:-
August 11, 2023
Virus Type:- Malware Loader
Severity:-
Medium
It has been reported that a new variant of malicious ChromeLoader extension called “Shampoo” is infecting users via fake advertisement activity. ChromeLoader is a component of Google Chrome browser extension malware, capable of installing malicious extensions in Google Chrome for advertising purposes. This extension can collect sensitive personal information, including search queries, and has the ability to redirect searches and inject advertisements into the victim's browsing session.
Infection Mechanism:
ChromeLoader Shampoo spreads through a network of malicious websites that falsely promise free downloads of games, music, movies, and more. When a victim attempts to download the desired content, instead of receiving the original file, they unknowingly download a VBScript. This VBScript executes a PowerShell script that sets a task prefixed with "chrome_" to ensure its continuation.
The assigned task proceeds to download a new PowerShell script into the host's registry, and further installs a malicious Chrome extension called Shampoo. Later, it links to the Chrome session and starts sending sensitive information to the C2 server.
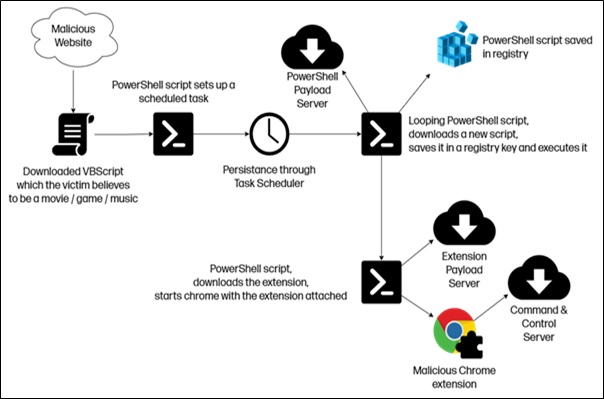
Shampoo is capable of disabling the search suggestion in the address bar and redirecting Yahoo, Google, and Bing searchers to the C2 server and also averts victims from accessing chrome://extensions by redirecting them to chrome://settings.
Shampoo ChromeLoader operates on loop scripts. If the victim attempts to reinstall the extension by rebooting the device or removing it, Windows will schedule the task to reinstall the extension.
Indicator of Compromise:
URLs
- mysitesext[dot]com
- worldtimesext[dot]com
- cesprincipledecli[dot]com
- dogsfanext[dot]com
Registry:
- HKCU:\Software\Mirage Utilities\Licence Protector
Folders:
- %LOCALAPPDATA%\chrome_display\
- %LOCALAPPDATA%\chrome_test\
- %LOCALAPPDATA%\chrome_performance\
Hashes:
- Cocaine Bear.vbs : eaf8a42542aa5b50c557010b00e00533561bac8a8520f94e718d9c20db7d52ef
- Background.js : cdb89fa263f512d396020efee1396dc1ac2eda17f4d5a2f7c0177d4a1d8b9744
For more detailed list of IoC, kindly refer the following URL:
Countermeasures:
- It is recommended to update to the latest version of Google Chrome to ensure the most up-to-date security protections.
- To get rid of ChromeLoader Shampoo, users can perform the following steps:
- Remove any scheduled tasks prefixed with "chrome_". Legitimate Chrome scheduled tasks are normally prefixed with "Google".
- Delete the registry key "HKCU\Software\Mirage Utilities\".
- Then reboot the computer.
- PowerShell scripts extracting the malicious extension to 'C:\Users\<user>\appdata\local\chrome_test' folder, which should be deleted if it exists.
- These removal steps must be completed quickly before the looping script reinstalls the malware.
- Regularly check the list of downloaded extensions.
- Download applications & extensions from official platforms and sources.
- Refrain using pirated software, instead use genuine software only.
- Download security solutions that can detect and block malicious components in seemingly legitimate software.
- Read all security warnings, license agreements, and privacy statements that are associated with any software that you download.
- Never click "Agree" or "OK" to close a window that you suspect might be spyware. Instead, click the red "x" in the corner of the window or press Alt + F4 on your keyboard to close a window.
- Be wary of popular "free" music and movie file-sharing programs, and make sure that you understand all the software packaged with those programs
- Do not download and install applications from untrusted sources [offered via unknown websites/ links on unscrupulous messages]. Install applications downloaded from reputed application market only. Users must be aware while clicking on links during web search
- Use a standard user account instead of an administrator account. An administrator account can access anything on the system, and any malware run with an administrator account can use the administrator permissions to potentially infect or damage any files on the system.
- Update software and operating systems with the latest patches. Outdated applications and operating systems are the targets of most attacks.
- Don't open attachments in unsolicited e-mails, even if they come from people in your contact list, and never click on a URL contained in an unsolicited e-mail, even if the link seems benign. In cases of genuine URLs close out the e-mail and go to the organization’s website directly through browser.
- It is advised to block office applications from creating executable files.
- Install ad blockers to combat exploit kits such as Fallout that are distributed via malicious advertising.
- Prohibit external FTP connections and blacklist downloads of known offensive security tools.
- All operating systems and applications should be kept updated on a regular basis. Virtual patching can be considered for protecting legacy systems and networks. This measure hinders cybercriminals from gaining easy access to any system through vulnerabilities in outdated applications and software. Avoid applying updates / patches available in any unofficial channel.
- Restrict execution of Power shell /WSCRIPT in an enterprise environment. Ensure installation and use of the latest version of PowerShell, with enhanced logging enabled. Script block logging and transcription enabled. Send the associated logs to a centralized log repository for monitoring and analysis.
- Establish a Sender Policy Framework (SPF) for your domain, which is an email validation system designed to prevent spam by detecting email spoofing by which most of the ransomware samples successfully reaches the corporate email boxes.
- Application whitelisting/Strict implementation of Software Restriction Policies (SRP) to block binaries running from %APPDATA% and %TEMP% paths. Ransomware sample drops and executes generally from these locations.
- Users are advised to disable their RDP if not in use, if required, it should be placed behind the firewall and users are to bind with proper policies while using the RDP.
- Block the attachments of file types, exe|pif|tmp|url|vb|vbe|scr|reg|cer|pst|cmd|com|bat|dll|dat|hlp|hta|js|wsf
- Consider encrypting the confidential data as the ransomware generally targets common file types.
- Perform regular backups of all critical information to limit the impact of data or system loss and to help expedite the recovery process. Ideally, this data should be kept on a separate device, and backups should be stored offline.
- Network segmentation and segregation into security zones - help protect sensitive information and critical services. Separate administrative network from business processes with physical controls and Virtual Local Area Networks.
References:
- https://threatresearch.ext.hp.com/shampoo-a-new-chromeLoader-campaign
- https://www.darkreading.com/endpoint/-shampoo-chromeLoader-variant-difficult-wash-out
- https://www.bleepingcomputer.com/news/security/new-shampoo-chromeLoader-malware-pushed-via-fake-warez-sites
- https://cyware.com/news/new-chromeLoader-variant-pushed-via-fake-websites-f5f1d05a


