SupremeBot Malware
Original Issue Date:-
August 11, 2023
Virus Type:- Trojan
Severity:-
Medium
It has been reported that a new trojanized Super Mario Bros game installer is being circulated, which contains various malicious components, including the SupremeBot mining client, XMR miner, and the Open-source Umbral stealer.
The malware is capable of stealing sensitive information and Valuable data, financial losses, etc.
Infection Mechanism
Due to Mario's immense popularity as an entertaining game with millions of downloads, threat actors have taken advantage of this by distributing a modified version of the game's installer through various channels such as social media, phishing etc. This tempered Mario installer is spread as a self-extracting archive executable.

After being tampered with, Mario's installer file "Super-Mario-Bros.exe" is transformed into a trojan-infected variant of a Super Mario game installer, consisting of three executable files in which the "super-mario-forever-v702e.exe" represents the main, safe, and genuine application of the Mario game, among three executable files. Additionally, there exist two malicious executable files named "java.exe" and "atom.exe." During the game installation process, these files secretly find their way into the victim's AppData directory.
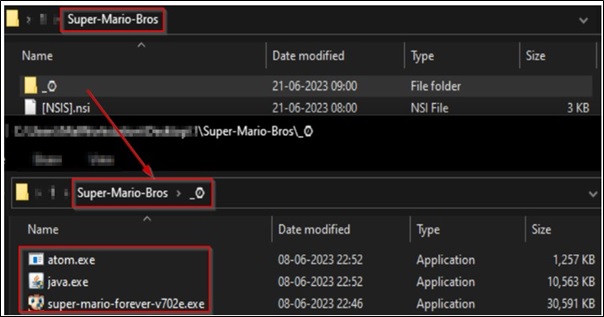
Once the malicious executables have been stored on the disk, these are executed by the installer to initiate the operation of an XMR (Monero) miner and a SupremeBot mining client. The malware gathers data about the target's hardware and establishes a connection with a mining server in order to initiate mining operations.
Within the game's installation directory, "atom.exe" (SupremeBot) generates a replica of its own file and conceals it within a hidden folder.
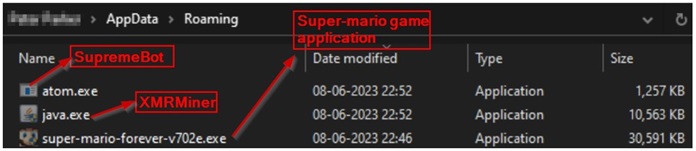
Following this, it sets up a recurring task that triggers the duplicate file every 15 minutes without an end, cleverly disguising itself under the guise of a legitimate process.
Umbral Stealer also execute to steal Windows-based information with the help of the C2 server.
Indicator of Compromise:
Super Mario Bros Installer:
- MD5- 90647ec1bc00c6d35ba3fd7ee214cd20
- SHA1- 0eb317fb165e87c23770ab6dff45e92dbd209b66
- SHA256- e9cc8222d121a68b6802ff24a84754e117c55ae09d61d54b2bc96ef6fb267a54
Atom.exe (SupremeBot)
- MD5- 54d4bcd4e789a196022632e1f0922dd7
- SHA1- 41ff5729fdeafec9879f12faffa3a62391e0a6f5
- SHA256- 41d1024209b738785ace023c36b2165d95eab99b0d892327212b8a5f7c311610
URL: (connect from SupremeBot)
- hxxp://silentlegion[.]duckdns[.]org/gate/update[.]php
- hxxp://silentlegion[.]duckdns[.]org/gate/connection[.]php
- hxxp://silentlegion[.]duckdns[.]org/gate/config[.]php
For more detailed list of IoC, kindly refer the following URL:
Best Practices and Recommendations:
- It is advisable for users to periodically check their system performance and CPU usage.
- Enterprises ought to take measures to prevent users from downloading pirated software from Warez/Torrent websites, as the presence of malware in "Hack Tool" found on sites like YouTube, Torrent sites, etc., is a concern.
- The organizational information security policies/acceptable usage policies should be revised to explicitly prohibit the downloading and installation of crypto mining software on end-user systems.
- Users are encouraged to enable the automatic software update feature on their computer, mobile, and other connected devices.
- It is recommended to use a reputable antivirus and internet security software package on connected devices, such as PCs, laptops, and mobile devices.
- As part of ongoing security awareness and training, users should be educated not to open untrusted links and email attachments without first verifying their authenticity.
- Only click on URLs that clearly indicate the website domain. When in doubt, users can search for the organisation's website directly using search engines to ensure that the websites they visited are legitimate, to protect themselves from threats like phishing attacks and untrusted URLs.
- URLs that could be used to distribute malware, such as Torrent/Warez, should be blocked.
- It is important to monitor endpoints and servers for unexpected spikes in CPU and RAM utilization, which could indicate a potential malware infection.
- Carry out vulnerability Assessment and Penetration Testing (VAPT) and information security audit of critical networks/systems, especially database servers from CERT-IN empanelled auditors. Repeat audits at regular intervals.
- Individuals or organizations are not encouraged to pay the ransom, as this does not guarantee files will be released. Report such instances of fraud to CERT-In and Law Enforcement agencies.
References:
- https://blog.cyble.com/2023/06/23/trojanized-super-mario-game-installer-spreads-supremebot-malware
- https://www.bleepingcomputer.com/news/security/trojanized-super-mario-game-used-to-install-windows-malware
- https://securityaffairs.com/147809/malware/trojanized-super-mario-bros-game.html?web_view=true


