ViperSoftX Malware
Original Issue Date:- May 03, 2023
Virus Type:- Remote Access Trojan
Severity:- High
It has been reported that a new version of the ViperSoftX information-stealing malware is spreading, featuring sophisticated encryption methods and anti-analysis techniques such as byte remapping and web browser communication blocking. The latest version of this JavaScript-based Remote Access Trojan (RAT) has enhanced capabilities to target password managers and scans for the presence of KeePass 2 and 1Password password managers. The threat actors behind the malware deployed carriers in the form of fake software update for multimedia editors, video format converters, or cryptocurrency apps. The Windows malware targets Brave, Google Chrome, Microsoft Edge, Mozilla Firefox, and Opera browsers, and uses several anti-detection, anti-analysis, and stealth-boosting features.
Infection Mechanism
ViperSoftX is a JavaScript-based Remote Access Trojan and cryptocurrency hijacker that arrives as software cracks, activators, or key generators, hiding within benign-appearing software. The latest version masquerades as a fake software update for multimedia editors, video format converters, or cryptocurrency apps. This is a Windows malware and downloads a VenomSoftX PowerShell installer from the C&C server and extracts the browser extension, modifying the link file with a parameter to load the malicious extension. The VenomSoftX extension has a broad list of abilities: giving the cyber criminals full access to visited websites, doctoring cryptocurrency addresses and other data (including log-in credentials) on crypto exchange websites. The malicious browser extension payload VenomSoftX carries out man-in-the-browser attacks, tampering with API requests from popular cryptocurrency exchanges and draining victims' accounts. The ViperSoftX RAT uses strong obfuscation methods, which complicate its detection and analysis. Amongst these techniques is disguising its malicious code under seemingly legitimate names and parts of encrypted code (AES cryptographic algorithm).
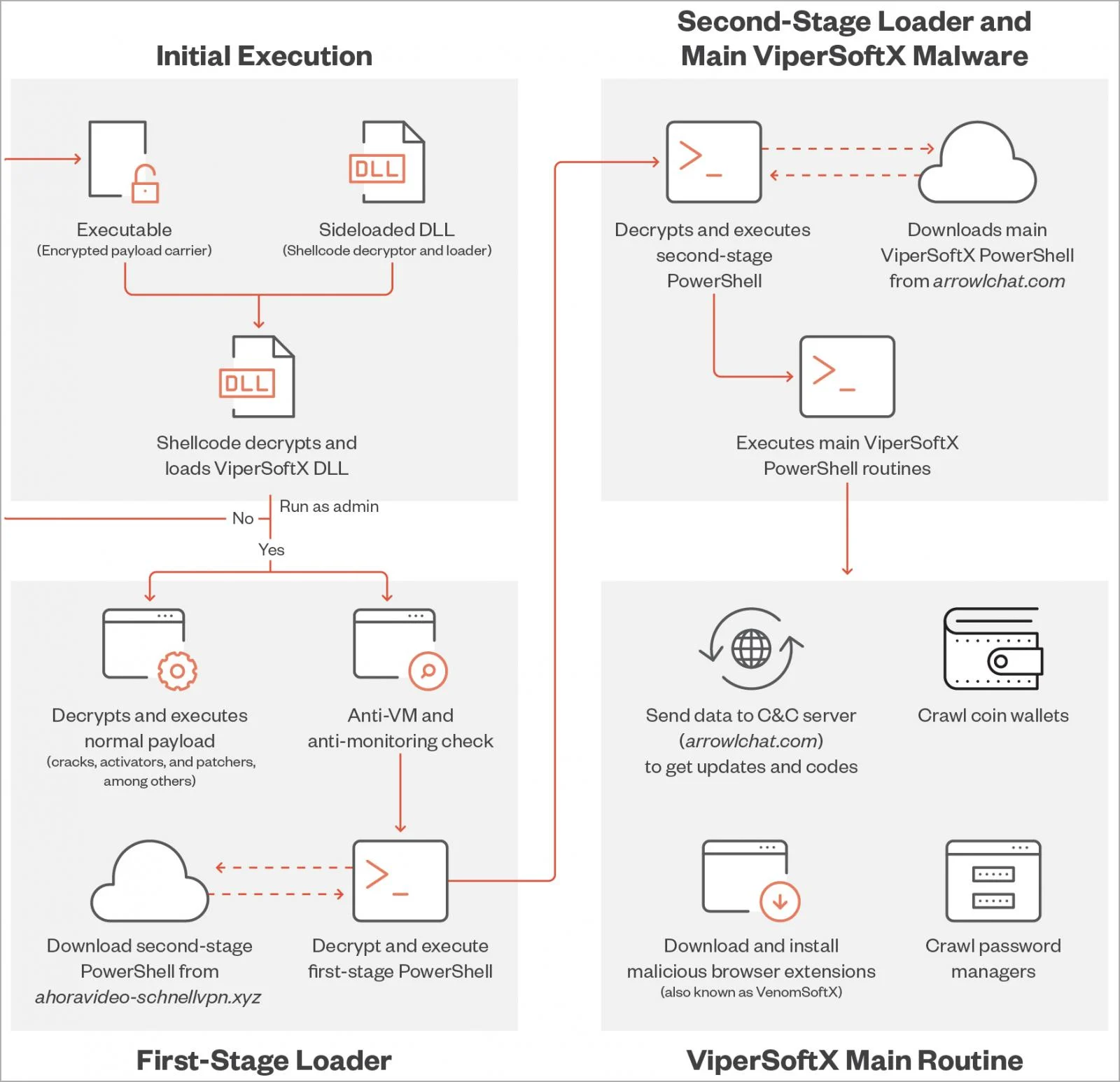
Indicators of Infection
Hashes:
- A list of indicators can be found in this text file
Best practices and remedial measures:
Recommendations to prevent the risks of infection from malware types like ViperSoftX:
- Download software and applications from official platforms and sources.
- Refrain using pirated software, instead use genuine software only.
- Download security solutions that can detect and block malicious components in seemingly legitimate and non-malicious software and applications.
- Read all security warnings, license agreements, and privacy statements that are associated with any software that you download.
- Never click "Agree" or "OK" to close a window that you suspect might be spyware. Instead, click the red "x" in the corner of the window or press Alt + F4 on your keyboard to close a window.
- Be wary of popular "free" music and movie file-sharing programs, and make sure that you understand all the software packaged with those programs
- Use a standard user account instead of an administrator account. An administrator account can access anything on the system, and any malware run with an administrator account can use the administrator permissions to potentially infect or damage any files on the system.
- Do not download and install applications from untrusted sources [offered via unknown websites/ links on unscrupulous messages]. Install applications downloaded from reputed application market only. Users must be aware while clicking on links during web search
- Update software and operating systems with the latest patches. Outdated applications and operating systems are the targets of most attacks.
- Don't open attachments in unsolicited e-mails, even if they come from people in your contact list, and never click on a URL contained in an unsolicited e-mail, even if the link seems benign. In cases of genuine URLs close out the e-mail and go to the organization’s website directly through browser.
- Install ad blockers to combat exploit kits such as Fallout that are distributed via malicious advertising.
- Prohibit external FTP connections and blacklist downloads of known offensive security tools.
- All operating systems and applications should be kept updated on a regular basis. Virtual patching can be considered for protecting legacy systems and networks. This measure hinders cybercriminals from gaining easy access to any system through vulnerabilities in outdated applications and software. Avoid applying updates / patches available in any unofficial channel.
- Restrict execution of Power shell /WSCRIPT in an enterprise environment. Ensure installation and use of the latest version of PowerShell, with enhanced logging enabled. Script block logging and transcription enabled. Send the associated logs to a centralized log repository for monitoring and analysis.
- Users are advised to disable their RDP if not in use, if required, it should be placed behind the firewall and users are to bind with proper policies while using the RDP.
- Block the attachments of file types, exe|pif|tmp|url|vb|vbe|scr|reg|cer|pst|cmd|com|bat|dll|dat|hlp|hta|js|wsf
- Perform regular backups of all critical information to limit the impact of data or system loss and to help expedite the recovery process. Ideally, this data should be kept on a separate device, and backups should be stored offline.
- Network segmentation and segregation into security zones - help protect sensitive information and critical services. Separate administrative network from business processes with physical controls and Virtual Local Area Networks
References:


